Email and HIPAA Compliance in Your Business
When you think of email from a business standpoint you think of company announcements, junk mail, co-worker problem solving, and reminders that it's Jane's birthday. It is easy to get caught up in the flow of the business and overlook the full functions of this tool that you use every day. This is true even more so in health care because the focus tends to lean more on patient satisfaction than it does the technical aspects in the background. This is why email often gets overlooked when it comes to HIPAA compliance.
Thanks to the guidelines and regulations set by HIPAA, this vital tool to your practice must be considered when assessing compliance. Now, the series of questions you may have probably look like this:
- What makes email compliant?
- Is it a click of a button?
- Is it costly?
- Is it mandatory?
Before these questions can be addressed you must first address how your company uses email. Essentially, if you are emailing electronic personal health information (ePHI) for whatever reason you must be HIPAA compliant. The guidelines for compliance vary by how you are emailing and to whom you are emailing, but there are guidelines to follow regardless of which method you are using.
Your email MUST be HIPAA compliant if:
- Email is used to send any ePHI outside of your domain.
- Email is used to send ePHI only within in your domain AND your email network is not behind a firewall.
- Email is used to send referrals to other doctors, communicate with patients, send prescriptions to the pharmacy, communicate with insurance companies, etc.
- Email is used to communicate with employees only within your network behind a firewall*
*NOTE: In this instance, you do not need to comply with the email encryption requirement, but your email must still comply with other HIPAA safeguards within your network.
So basically, as a HIPAA covered entity, there HIPAA regulations you must follow if you are using email in pretty much any capacity within your organization.
Email Specific HIPAA Regulations
Now that the usage has been defined, let’s look at HIPAA for a second. According to HIPAA regulations, depending on the way you are using email there are several things that need to be considered and actions to take that make compliance possible. Whether you choose to host your own email server or have your email through a hosted email provider there are actions to be taken.
All Email
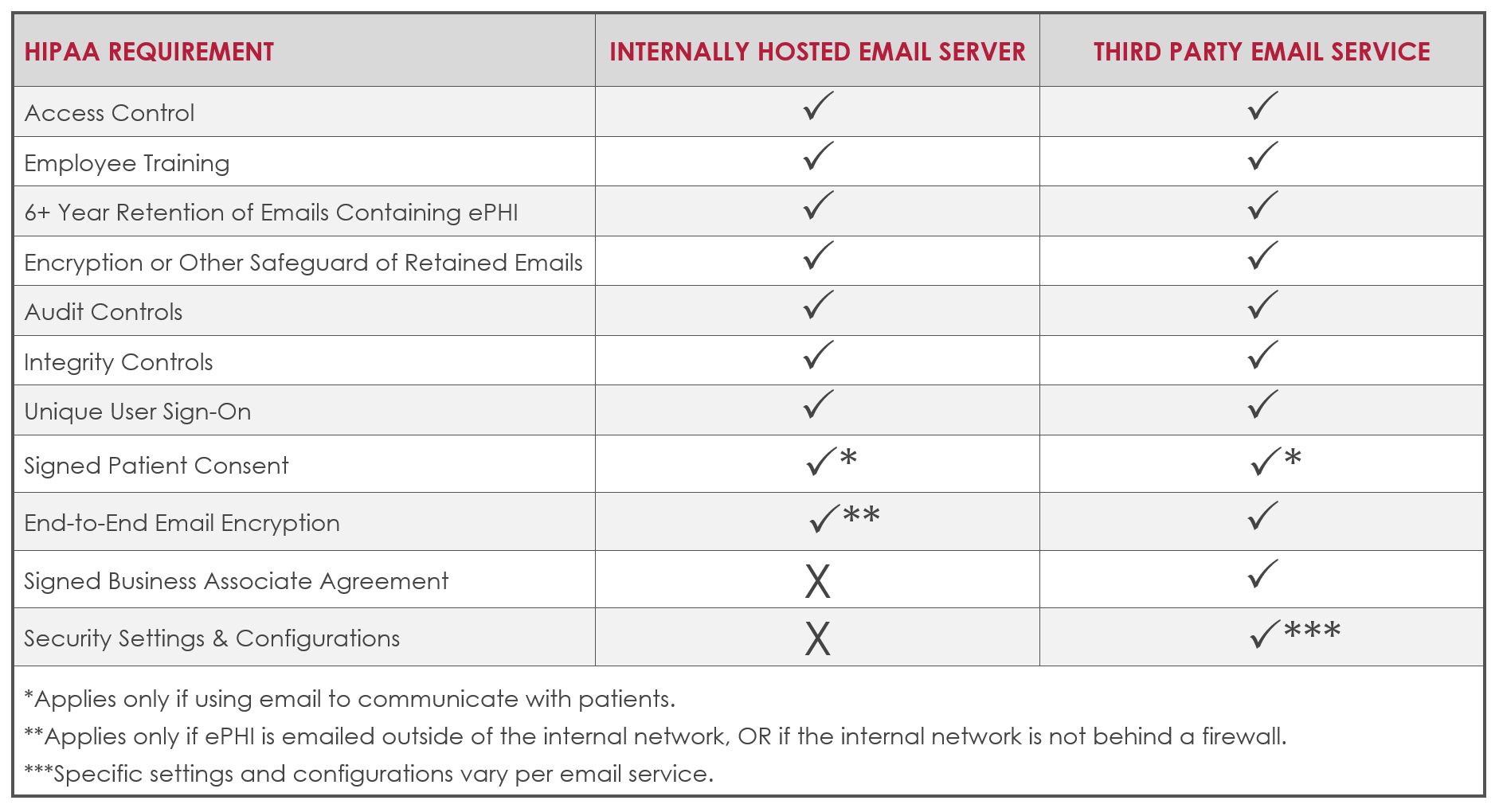
HIPAA covered entities using email in ANY capacity must take the following actions:
- Implement access control safeguards and policies and procedures. Access controls limit access to ePHI to only individuals who need it, but also include policies and procedures that document which employees require various levels of access, and how ePHI may be shared under various circumstances.
- Conduct and document employee training on sending emails containing ePHI correctly.
- All emails containing ePHI must be retained for at least 6 years or per the retention guidelines set by your individual state, whichever is longer.
- All retained emails must be encrypted within your network or have another safeguard in place to prevent access.
See HIPAA Administrative Simplification § 164.312(c)(2)(ii).
- Audit controls must be in place to ensure all policies and procedures are being followed. Audit controls include hardware, software, and procedural systems that document and analyze the use and activity within information systems that contain or access ePHI. In January 2017, the OCR published a newsletter detailing HIPAA audit control requirements.
- Integrity controls must be in place to prevent emails from being deleted or altered.
- Each user must have their own, unique email and network sign on that is not shared with any other individual.
Email Communication with Patients
It is also important to note that if email is used to communicate with patients, no matter which method you are choosing, the practice needs signed consent from the patient as well as documentation that you informed them of the potential risks prior to doing so.
Internally hosted email server
In addition to the above requirements, an additional encryption requirement applies if you host email on an internal server and are sending ePHI outside of your network, or if there is no firewall in place.
- You must have end-to-end encryption on email. End-to-end encryption prevents third party access to the information being sent by encrypting the data on the sender's network and only allowing the receiver to decrypt it. Currently AES 128, 192, or 256-bit encryption is recommended (HIPAA).
Email hosted through an email provider
Specific HIPAA requirements also apply if you utilize email hosted through a third party email provider (i.e. Microsoft Office 365, Google G Suite, GoDaddy, etc.).
Most hosted email providers are not HIPAA compliant out of the box, but many can be used in a compliant way with appropriate configuration and training. Necessary configurations and settings vary per provider, most hosted email solutions offer various security settings and configurations. All HIPAA-applicable email security settings must be turned on and configured appropriately. These settings are typically not set for HIPAA compliance by default and necessary configurations are unique to the organization.
In addition to turning on appropriate security settings and configurations, the following requirements also apply in a hosted email setting:
- You must obtain a signed Business Associate Agreement (BAA) with the third party email provider. Many providers like Google G Suite provide their own BAA. Even if your email provider offers a BAA, it is the covered entities' responsibility to know if and when the BAA is required. (i.e. You are at fault, not Google if you are required to have a BAA in place with them and do not sign one.)
- You must have end-to-end encryption on all email sent via the third party provider, including emails sent within the hosted domain and to external domains. End-to-end encryption prevents third party access to the information being sent by encrypting the data on the sender's network and only allowing the receiver to decrypt it. Currently AES 128, 192, or 256-bit encryption is recommended (HIPAA).
Putting it All Together
As with all HIPAA regulations, email compliance is not black and white. It depends on the unique risks within your policies, procedures, systems, and uses within your practice or business. HIPAA places the burden of responsibility on you to understand your own risks and implement the appropriate HIPAA guidelines to adequately mitigate those risks.
These are the email applicable HIPAA guidelines, but how you adopt the applicable guidelines is unique to your own risks. Your HIPAA risk analysis is the best tool to identify your risks, identify applicable regulations, and how you must address your risk.
These steps can take time to implement and if you are uncertain if the steps you are taking are not compliant it is always best to reach out to your legal and/or IT team.
About Kayla Wharton
Kayla has a Bachelor of Science in Business Administration from Shepherd University and will earn her Master's Degree in Health Information Management from University of Maryland University College (UMUC) in October 2019. She joined Innovative in May 2016 as Operations Coordinator and transitioned to HIPAA Compliance Specialist in October 2017. Kayla loves sharing her passion for data security and compliance with Innovative's customers.




